Global Automated Breach and Attack Simulation Market Size, Share, Trends, & Growth Forecast Report By Type (Software, Services), Application (Configuration Management, Patch Management, Threat Intelligence, Team Assessment, and Others), End User Industry (Enterprises, Data Centers and Service Providers) & Region, Industry Forecast From 2024 to 2033
Global Automated Breach and Attack Simulation Market Size
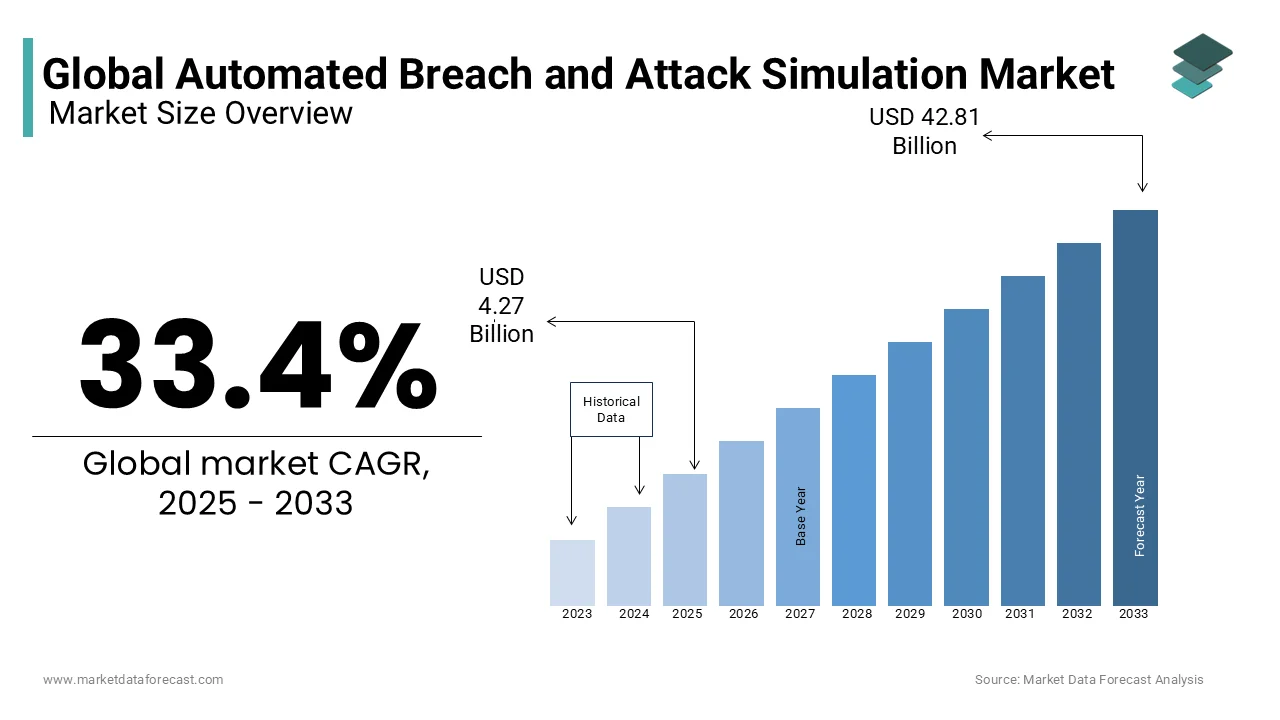
The global automated breach and attack simulation market was worth USD 3.2 billion in 2024. The global market is predicted to reach USD 4.27 billion in 2025 and USD 42.81 billion by 2033, growing at a CAGR of 33.4% during the forecast period 2025 to 2033.
In this modern world, the need to improve the security systems of the computer to protect from breachers is highly important. Breach and attack simulations are the advanced techniques used in computer security testing methods. In the software, there is a high risk of data breaches and other security issues, which is why there is a need to identify vulnerabilities in the overall software infrastructure. According to the latest survey reports, more than 30 million malware samples were detected in 2023. The prominence of adopting high-security testing methods for both laptops and computers is significant in leveling up the growth rate of the automated breach and attack simulation market. Breach and attack simulations help to check out any vulnerabilities in the overall computer security system and enable to detect the threats, if there are any so that it allows to defend against the cyber-attacks by regularly sending the breach and attack simulation signals that effectively measure and manage the overall insight of an organization.
MARKET DRIVERS
The growing demand to protect organizations from data breaches is anticipated to fuel the growth rate of the automated breach and attack simulation market.
Automation in computer security testing methods eventually grabbed much attention due to its effective approach to testing and security. The rise in the popularity of data protection from various cyber-attacks is causing the market to grow to the next level.
We are living in a digital world where almost 90% of financial activities are thoroughly activated through digital payment methods. Automated breach and attack simulation is an important aspect of protecting the system in the finance sector to deliver high protection and prevent data breaches. According to the Indian Cyber Crime Coordination Centre, India recorded 1.13 million cases of financial fraud cases in 2023. It is reported that the Indian government is making huge plans to prevent fraud cases online by randomly adopting advanced technologies. As per reports, more than 1200 crore rupees have been saved by the best technological developments.
The proper management of an organization's computer security system enables the prevention of high-security breach activities, even in the healthcare sector. Data breach issues happen very often in the healthcare sector. Nowadays, the growing prominence of the use of the Internet of Things in healthcare is ascribed to fixing the automation breach and attacking the simulation market. Cyber-attacks have become a major concern for healthcare. The US Department of Health and Human Services reportedly received a 256% rise in hacking-related breaches in the healthcare sector. More than 134 million individuals were affected due to cyber attacks in healthcare in 2023. In order to reduce or prevent the growing menace of cyber-attacks, the Healthcare Insurance Portability and Accountability Act (HIPAA) is steeping towards crucial insights in regulating the complex strategies to prevent cyber-attacks. Globally, around 80% of healthcare data breaches happen due to IT incidents and hacking. The consistency of the IT hacking incidents is increasing strongly, which is likely to propel the growth rate of the automated breach and attack simulation market.
MARKET RESTRAINTS
However, the lack of certain knowledge over the utilization of highly advanced techniques certainly limits the growth rate of the automated breach and attack simulation market.
The major issue in the IT sector is detecting internal vulnerabilities. Automated breach and attack simulation are highly effective in detecting the risks associated with various forms but not internal vulnerabilities like negligence of the employee and others. Many organizations face internal vulnerabilities in different ways that can be tested by pen testing, which impacts the growth rate of the market to an extent. The overall process is a bit difficult to understand, especially in terms of the accuracy of the threats and to analyze them at certain times, which eventually degrades the market’s growth rate. Understanding the complex process in the IT sector requires highly skilled professionals, and the availability of a minimal number of skilled professionals may also hinder the growth rate of the automated breach and attack simulation market. Many IT companies are still facing difficulty in recruiting skilled professionals to run automated testing methods in computer security, which is a major issue for the rising threats even after adopting advanced technologies in the IT sector.
MARKET OPPORTUNITIES
The automated breach and attack simulation market is deemed to have accountable growth opportunities in the coming years.
An incredibly growing number of people connected to the Internet of Things through smartphones is enabling data breaches to find a way to hack, which is dominantly resulting in rising risk factors. The automated breach and attack simulation helps potentially mitigate the risk of data breach from hackers by sending a report that helps prevent the risk from the breachers. Also, increasing support from both public and private organizations to adopt security testing methods to protect from cyber threats eventually promotes growth opportunities for the market in the coming years.
Machine learning and Artificial Intelligence (AI) have wide applications in the automated breach and attack simulation market. AI has the ability to perform specific tasks in sending breach and attack simulation pathways. It is augmented to deliver the best capability of delivering high-quality responses over threat detection. AI algorithms are very effective in managing risks proactively, which defines a new future in cyber security applications.
The growing importance of the development of proper IT infrastructure with special specifications to protect organizations also influences the growth rate of the automated breach and attack simulation market. Rising awareness over the availability of various techniques to evaluate the security infrastructure and to evaluate the vulnerabilities before any attack occurs in real-time. This attribute greatly influences the growth rate of the market.
MARKET CHALLENGES
The lack of proper infrastructure facilities for IT, especially in undeveloped countries, is certainly a challenging factor for the automated breach and attack simulation market.
Due to a lack of investments from government officials and people’s reluctance to adopt the Internet of Things solutions, the demand for testing methods in undeveloped countries is very low. However, few countries anticipate adopting these new changes in controlling cyber attacks and elevating their dominance in the IT sectors.
REPORT COVERAGE
|
REPORT METRIC |
DETAILS |
|
Market Size Available |
2024 to 2033 |
|
Base Year |
2024 |
|
Forecast Period |
2025 to 2033 |
|
CAGR |
33.4% |
|
Segments Covered |
By Type, Application, End-User, And Region |
|
Various Analyses Covered |
Global, Regional & Country Level Analysis, Segment-Level Analysis, DROC, PESTLE Analysis, Porter’s Five Forces Analysis, Competitive Landscape, Analyst Overview on Investment Opportunities |
|
Regions Covered |
North America, Europe, APAC, Latin America, Middle East & Africa |
|
Market Leaders Profiled |
Qualys (US), Rapid7 (US), DXC Technology (US), AttackIQ (US), Cymulate (Israel), XM Cyber (Israel), Skybox Security (US), SafeBreach (US), Firemon (US), Verdoin (FireEye) (US), NopSec (US), Threatcare (US), Mazebolt (US), Scythe (US), and Cronus-Cyber Technologies (Israel) among others. |
SEGMENTAL ANALYSIS
By Type Insights
The software segment is leading with the dominant share of the market owing to the rising number of people using various smartphone applications. The demand to validate the organization’s security posture with various testing methods is escalating the growth rate of the market. The increasing scale of the IT sector and the rising prominence of high-security testing methods to avoid cyber attacks are greatly influencing the share of the software segment. The services segment is likely to have the fastest growth opportunities throughout the forecast period.
By Application Insights
The configuration management segment is ruling with the prominent share of the automated breach and attack simulation market. In the IT sector, it is most common to track, manage, and control the changes in the software’s configuration, which can be done easily through configuration management. It is a major aspect of the overall software system that helps constantly control and configure the security controls that figure out threats. Threat intelligence systems are likely to hit the highest CAGR by the end of the forecast period. Identifying the threats before a real attack occurs is usually a prominent process to follow in every organization to avoid the risk of vulnerabilities in various ways. Therefore, the demand for threat intelligence is growing at a higher rate these days.
By End-User Insights
The enterprise segment is greatly influencing the growth rate of the automated breach and attack simulation market. The landscape of the IT sector is evolving, and there is a need to simulate and mimic threats to identify the errors that help fill in gaps before any real cyber-attacks occur. Regularly checking on these updates will eventually escalate the growth rate of the automated breach and attack simulation market. The data centers segment is next in leading the dominant market’s size.
REGIONAL ANALYSIS
North America's automated breach and attack simulation market is leading, with the dominant share owing to the presence of a large number of IT companies. According to the International Trade Administration, there are around 585,000 IT companies only in the US, and 13,400 of these are start-ups established in 2019 alone. These companies are sustained in developing various software applications that potentially increase the need for cybersecurity, which intensifies the growth rate of the automated breach and attack simulation market. The USA is the global leader in industrial technology, where top companies like Google, Meta, Apple, Microsoft, and others were established in the US that changed the living style of people around the world to the next level. The rising standard towards digitalization is one of the major factors attributed to the rising cyber-attacks. The breachers are finding a new solution to hack the system with the evolving technology, which is intensifying the growth rate of the automated breach and attack simulation market.
Asia Pacific is next in leading the dominant size of the automated breach and attack simulation market. Top companies are showing interest in the expansion of their portfolio by launching the company footprints in various regions. India and China have evolved and launched various IT companies in the past few years. Increasing support from the government authorities and collaborations between the top IT companies are leveraging the growth rate of the market. The penetration of software technology in healthcare is making tasks easy, which is dominantly leveraging the growth rate of the automated breach and attack simulation market. The importance of adopting testing methods in computer security is eventually growing in the healthcare sector to lower the risk of data breaches. In the time of COVID-19, India faced many challenges in protecting the data in the healthcare industry. According to media reports, almost eight crore Indian data was breached through the ICMR COVID site. Government authorities are taking stringent actions regarding the incidences and taking necessary steps to protect the data from breaches in various ways.
Europe's automated breach and attack simulation market growth rate is expected to reach the highest by the end of 2029. EU government authorities impose stringent rules and regulation techniques for the prevention of cyber attacks by regularly adopting the advanced features in the applications. The digital transformations were boosted by the emergence of the COVID-19 pandemic. Since then, the government has taken certain actions to ensure a high level of cybersecurity, which anticipates the adoption of automated breach and attack simulations in every organization.
KEY MARKET PARTICIPANTS
The major players involved in the automated breach and attack simulation market include Qualys (US), Rapid7 (US), DXC Technology (US), AttackIQ (US), Cymulate (Israel), XM Cyber (Israel), Skybox Security (US), SafeBreach (US), Firemon (US), Verdoin (FireEye) (US), NopSec (US), Threatcare (US), Mazebolt (US), Scythe (US), Cronus-Cyber Technologies (Israel), and others.
MARKET SEGMENTATION
This research report on the global automated breach and attack simulation market has been segmented and sub-segmented based on the type, application, end-user, and region.
By Type
-
Software
-
Services
By Application
-
Configuration management
-
Patch Management
-
Threat Intelligence
-
Team Assessment
-
Others
By End-User
-
Enterprises
-
Data Centers
-
Service Providers
By Region
-
North America
-
The United States
-
Canada
-
Rest of North America
-
-
Europe
-
The United Kingdom
-
Spain
-
Germany
-
Italy
-
France
-
Rest of Europe
-
-
The Asia Pacific
-
India
-
Japan
-
China
-
Australia
-
Singapore
-
Malaysia
-
South Korea
-
New Zealand
-
Southeast Asia
-
-
Latin America
-
Brazil
-
Argentina
-
Mexico
-
Rest of LATAM
-
-
The Middle East and Africa
-
Saudi Arabia
-
UAE
-
Lebanon
-
Jordan
-
Cyprus
-
Frequently Asked Questions
How do Automated Breach and Attack Simulation solutions differ from traditional penetration testing?
While traditional penetration testing involves manual, point-in-time assessments, ABAS solutions automate the process of simulating attacks continuously. They provide organizations with real-time insights into their security posture, allowing for proactive threat mitigation.
What are the primary challenges hindering the adoption of Automated Breach and Attack Simulation technology in certain regions?
Challenges such as the shortage of skilled cybersecurity professionals, concerns regarding the complexity of implementation and integration with existing security infrastructure, and budget constraints are hindering the adoption of ABAS technology in certain regions.
How do Automated Breach and Attack Simulation solutions address the evolving threat landscape, including zero-day attacks and advanced persistent threats (APTs)?
ABAS solutions utilize threat intelligence feeds and machine learning algorithms to simulate emerging threats, including zero-day attacks and APTs. By continuously updating their attack scenarios based on the latest threat intelligence, they help organizations stay ahead of evolving cyber threats.
What are the anticipated trends shaping the future of the Automated Breach and Attack Simulation market globally?
Anticipated trends include the integration of ABAS solutions with Security Orchestration, Automation, and Response (SOAR) platforms, the rise of AI-driven ABAS solutions for predictive threat modeling, increased adoption of cloud-based ABAS solutions, and strategic partnerships among ABAS vendors and cybersecurity service providers to offer comprehensive security solutions.
Related Reports
Access the study in MULTIPLE FORMATS
Purchase options starting from $ 2500
Didn’t find what you’re looking for?
TALK TO OUR ANALYST TEAM
Need something within your budget?
NO WORRIES! WE GOT YOU COVERED!
Call us on: +1 888 702 9696 (U.S Toll Free)
Write to us: [email protected]